Configure Azure IdP for Dev Portal
Kong offers OIDC support to allow Single-Sign-on for Konnect and the Dev Portal. This guide shows you how to configure Microsoft Azure for Dev Portal SSO.
Create an application in Azure
-
In Azure, navigate to App registrations.
-
Click New registration to register a new application:
-
Name the application.
-
Select Accounts in this organizational directory only for the Supported account type.
-
Select Web and enter the Dev Portal Redirect URI.
-
Save the application ID for later.
Configure the Azure application
-
Click New client secret, enter a description, select an expiration value, and click Add.
- Save the secret value for configuring Konnect.
-
Click Overview in the sidebar, then click the Endpoints tab.
-
Copy the OpenID Connect metadata document URL and open it in your browser:
-
Your browser will display a large JSON blob object. In the object, find and save the
issuervalue.The
issuervalue will be used as the provider URL when configuring SSO in Konnect.
Configure group claims in Azure
-
On your new application page in Azure, click Token configuration in the sidebar.
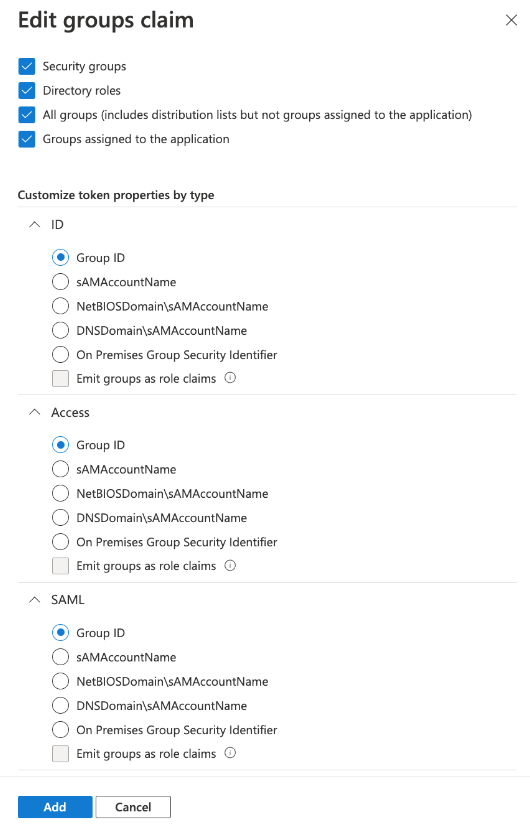
- Click Add groups claim and do the following:
- Select each checkbox in the Select group types to include in Access, ID, and SAML tokens section.
- Select Group ID for each section in Customize token properties by type.
- Click Add.
-
Click Add optional claim, select ID as the token type, and email as the claim.
- Click Add.
Configure SSO in Konnect
From the Konnect portal identity page, click Configure provider for OIDC, and enter the values from Azure.
This table maps the Konnect values to the corresponding Azure values.
| Konnect value | Azure value |
|---|---|
| Provider URL | The value stored in the issuer variable. |
| Client ID | Your Azure application ID. |
| Client Secret | Azure client secret. |
You can test your configuration by navigating to the Dev Portal and using your Azure credentials to log in.












