When the DPP runs:
- The
kuma-dp retrieves Envoy startup configuration from the control plane.
- The
kuma-dp process starts Envoy with this configuration.
- Envoy connects to the control plane using XDS and receives configuration updates when the state of the mesh changes.
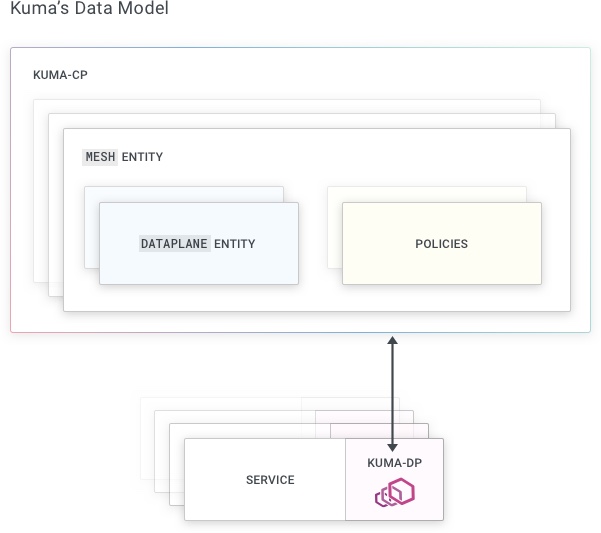
The control plane uses policies and Dataplane entities to generate the DPP configuration.
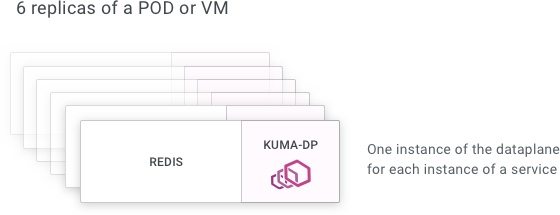
The kuma-dp process and its child process offer a number of services, these services need to listen to a few ports to provide their functionalities.
When we start a data-plane via kuma-dp we expect all the inbound and outbound service traffic to go through it. The inbound and outbound ports are defined in the dataplane specification when running in universal mode, while on Kubernetes the service-to-service traffic always runs on port 15001.
In addition to the service traffic ports, the data plane proxy also opens the following ports:
- TCP
-
9901: the HTTP server that provides the Envoy administration interface, It’s bound onto the loop-back interfaces, and can be customized using these methods:
- On Universal: data field
networking.admin.port on the data plane object
- On Kubernetes: pod annotation
kuma.io/envoy-admin-port
-
9902: an internal HTTP server that reports the readiness of current data plane proxy, this server is consumed by endpoint /ready of the Envoy Admin API. It can be customized using these methods:
- On Universal: environment variable on the data plane host
KUMA_READINESS_PORT
- On Kubernetes: on the control plane, set
KUMA_READINESS_PORT as part of the value of environment variable KUMA_RUNTIME_KUBERNETES_INJECTOR_SIDECAR_CONTAINER_ENV_VARS
-
9001: the HTTP server that provides the Application Probe Proxy functionalities. It can be customized using these methods:
- On Universal: environment variable
KUMA_APPLICATION_PROBE_PROXY_PORT.
- On Kubernetes: pod annotation
kuma.io/application-probe-proxy-port