This is the simplest deployment mode for Kong Mesh, and the default one.
- Zone control plane: There is one deployment of the control plane that can be scaled horizontally.
- Data plane proxies: The data plane proxies connect to the control plane regardless of where they are deployed.
- Service Connectivity: Every data plane proxy must be able to connect to every other data plane proxy regardless of where they are being deployed.
This mode implies that we can deploy Kong Mesh and its data plane proxies so that the service connectivity from every data plane proxy can be established directly to every other data plane proxy.
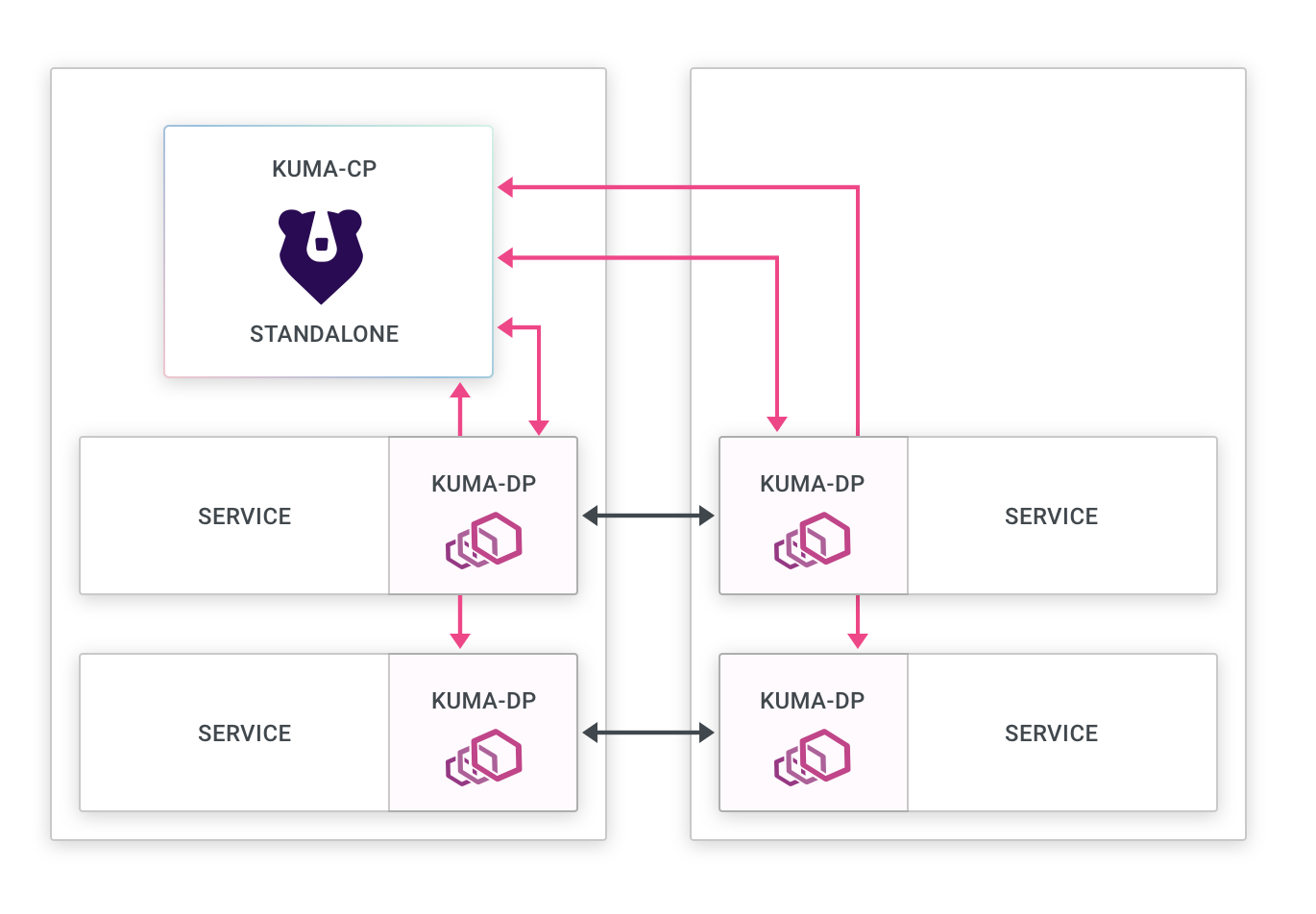
Single-zone mode is a great choice to start within the context of one zone (ie: within one Kubernetes cluster or one AWS VPC). You can then federate it into a multi-zone deployment.
To Install with this topology follow the single-zone deployment docs.