Kong Konnect
The SaaS API Platform
Introducing Konnect
Konnect is an API lifecycle management platform designed from the ground up for the cloud native era and delivered as a service. This platform lets you build modern applications better, faster, and more securely. The control plane is hosted in the cloud by Kong, while you can choose to either host the data plane yourself in your preferred network environment or let Kong manage it for you in the cloud. All of this is powered by Kong Gateway — Kong’s lightweight, fast, and flexible API gateway.
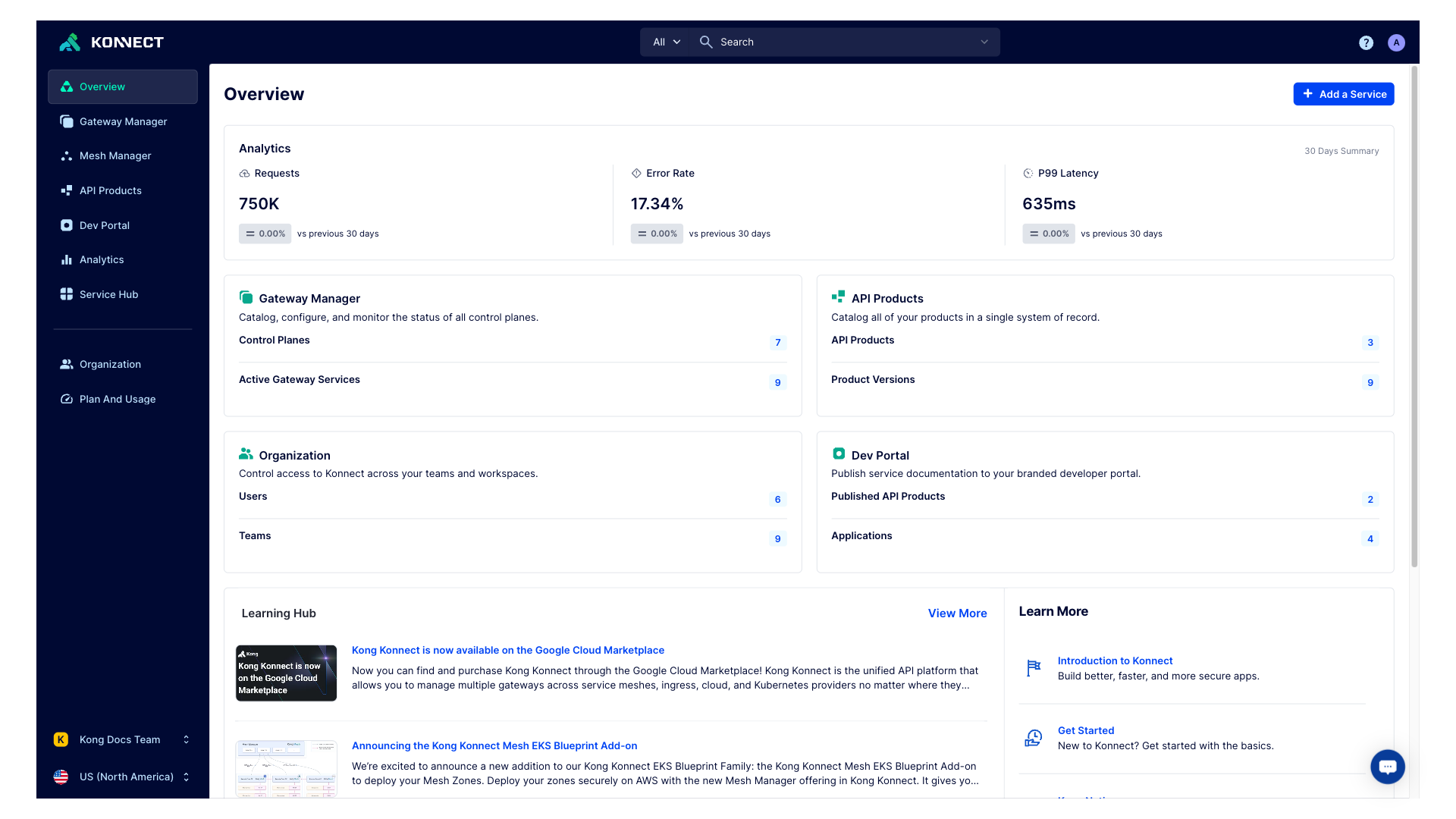
Konnect helps simplify multi-cloud API management by:
-
Offering the control plane to deploy and manage your APIs and microservices in any environment: cloud, on-premises, Kubernetes, and virtual machines.
-
Instantly applying authentication, API security, and traffic control policies consistently across all your services using powerful enterprise and community plugins.
-
Providing a real-time, centralized view of all your services. Monitor golden signals such as error rate and latency for each service and route to gain deep insights into your API products.
-
Control which geographic region the universal API control plane is operated in. AU, EU, and US geos are currently supported. This allows you to operate Konnect in a similar geographic region to your end-users, as well as ensure data privacy and regulatory compliance.
Konnect modules
Service Hub
Service Hub makes internal APIs discoverable, consumable, and reusable for internal development teams. You can use the Service Hub to catalog all your services and create a single source of truth for your organization’s service inventory. By leveraging Service Hub, your application developers can search, discover, and consume existing services to accelerate their time-to-market, while enabling a more consistent end-user experience across the organization’s applications.
Start cataloging services with Service Hub →
Gateway Manager
Gateway Manager instantly provisions a hosted Kong Gateway control plane and supports securely attaching self-hosted or managed data planes.
Through the Gateway Manager, increase the security of your APIs with out-of-the-box enterprise and community plugins, including OpenID Connect, Open Policy Agent, Mutual TLS, and more.
Learn more about the Gateway Manager →
Check out Konnect-compatible plugins →
Mesh Manager
Mesh Manager in Kong Konnect allows you to create, manage, and view your Kong Mesh service meshes using the Konnect platform. Mesh Manager is ideal for organizations who want to have one or more global control planes that allow you to run your mesh deployments across multiple zones. You can run a mix of Kubernetes and Universal zones. Your mesh deployment environments can include multiple isolated meshes for multi-tenancy, with workloads running in different regions, on different clouds, or in different data-centers.
Learn more about Mesh Manager →
API Products
Use API Products to bundle and manage multiple services via API products. You can use API products to version your services as well as upload documentation for your API product. This allows you to prepare to productize your services by publishing your API products to Dev Portal. Start productizing services with API Products →
Dev Portal
Streamline developer onboarding with the Dev Portal, which offers a self-service developer experience to discover, register, and consume published API products from your API Products catalog. This customizable experience can be used to match your own unique branding and highlights the documentation and interactive API specifications of your services. Enable application registration to automatically secure your APIs with a variety of authorization providers.
Learn more about the Dev Portal →
Analytics
Use Analytics to gain deep insights into service, route, and application usage and health monitoring data. Keep your finger on the pulse of the health of your API products with custom reports and contextual dashboards. In addition, you can enhance the native monitoring and analytics capabilities with Kong Gateway plugins that enable streaming monitoring metrics to third-party analytics providers, such as Datadog and Prometheus.
Konnect Analytics provides pre-built custom reports to all new organizations. These reports contains common examples for important key performance indicators (KPIs) to keep track of while monitoring the success of your APIs. Users are free to modify them, and use them as a base to start their own analytics reports.
Teams
To help secure and govern your environment, Konnect provides the ability to manage authorization with teams. You can use Konnect’s predefined teams for a standard set of roles, or create custom teams with any roles you choose. Invite users and add them to these teams to manage user access. You can also map groups from your existing identity provider into Konnect teams.












